I’m a pretty happy owner of a Samsung Galaxy S3, Android Version 4.1.2. I don’t know if these things apply to the Galaxy S3 only, or if it’s the Android system that’s broken, but I’m pretty sure a lot of these things apply to all Android 4.1.2 phones.
As you might have noticed I’m a little paranoid, so of course I want all security features enabled. Especially an encrypted internal memory and encrypted SD card is important. So while I wanted to set up the encryption for the internal memory, the device asked me to set up a lock screen password first, that contains at least one number.
First mistake. Why a number? There are enough reasons not to force such complexity rules. Maybe I would put a longer password in there with only lower and upper case. Now I have to press and hold one of the number buttons, which takes about 2 seconds. An alternative is to press 3 buttons to get a number. When you’re a fast typer you can type in 3 lowercase letters in that time, which is a lot stronger than having only a single number in it (if the attacker can still not rule out a number). Ok, whatever, let’s go on. But wait.
Second mistake. Why do I have to set up a lock screen password for device encryption? Answer: The disc encryption password is the lock screen password. Device encryption and lock screen are two different things. One scenario is a cold boot attack attacking the disc encryption password. The other one is when an attacker finds a device that is still running (let’s call it running device attack). If we want a shorter password for the lock screen for convenience reasons, then of course the security will decrease and running device attacks will get easier. But security does not decrease for cold boot attack scenarios if you’re able to use two different passwords. Of course you can argue that the running device attack is much more likely for mobile phones. But with some crypto you can easily make two different attack scenarios with different risks, depending on each password. So why do they have to be the same? The only conclusion I drawed at this point was that the disc encryption key will be properly wiped when the lock screen is enabled. So to unlock it you would need the disc encryption password (I was so wrong).
After setting the password I encrypted the SD card first, then the device. From that point on, I had to type in that long password every time I unlocked the screen. Annoying, but at least it’s secure as long as nobody is looking over my shoulder when I’m unlocking my phone (again, he would get the password for the cold boot AND the running device attack).
I took a month to think about the next security measure: Setting up SamsungDive. It’s the Samsung service where you can locate/wipe/ring your phone in case it got stolen or you lost it. I wasn’t sure if I wanted to do that. What if there is a security breach at samsungdive.com and somebody wipes my phone? And do I really want to give all that private information to Samsung? In the end I decided I wanted the feature anyway, so I set up a SamsungDive account. When I logged in, I realised there is another feature: Unlocking the screen remotely. Of course this would work for non-encrypted devices, but it won’t work for encrypted ones, because the encryption key was wiped when the screen was locked, right? Wrong.
Third mistake. The encryption key is not wiped when you lock your screen. It’s merely just to annoy the user that the lock screen password has to be the encryption password. After encrypting the device you can not change the lock screen type any more, everything is grayed out, except the password:
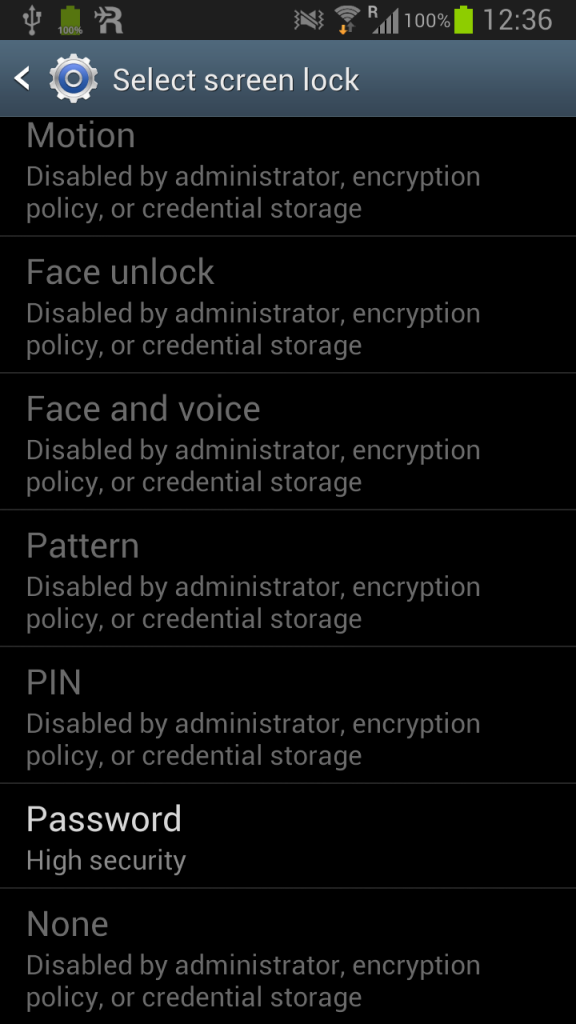
But let’s unlock the screen from the SamsungDive web site:
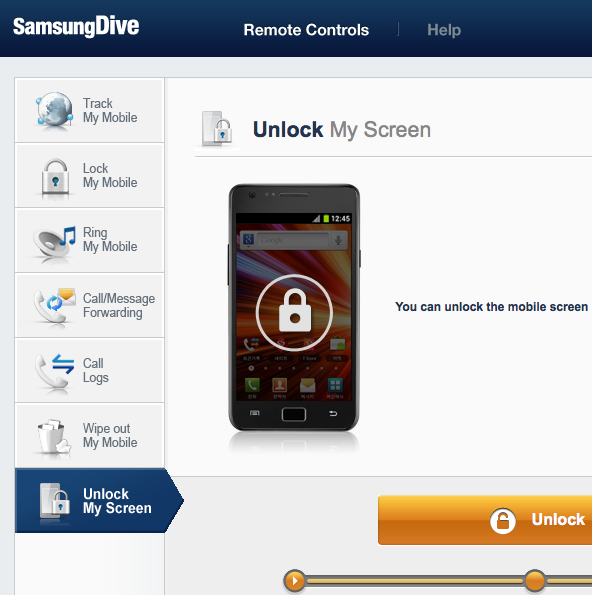
Now there is no screen lock anymore. Disabled. Gone. You don’t have to type in your password anymore. Look, swipe means no lock screen:
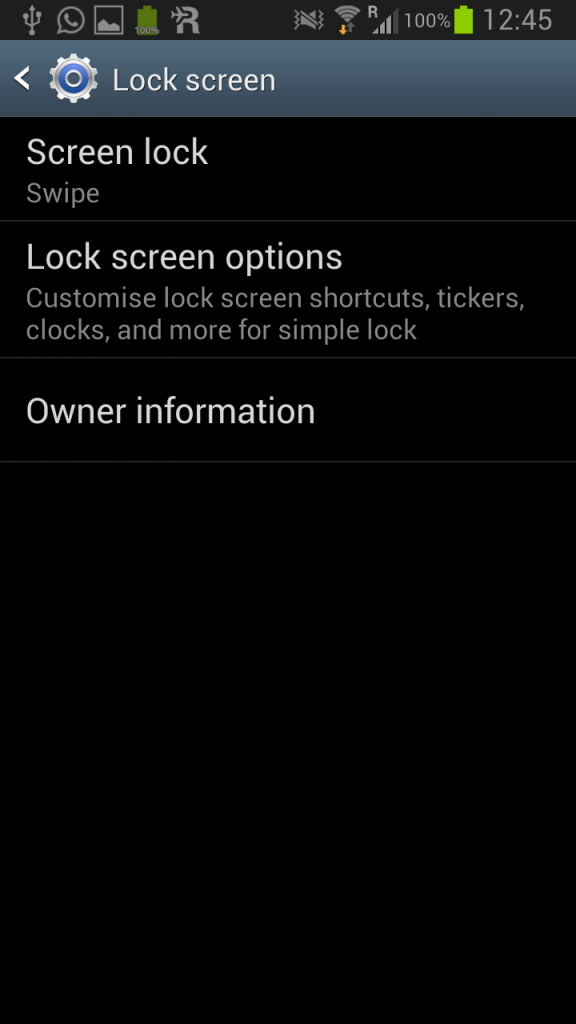
And when we want to change the type of lock screen mode again (clicking on Screen lock – Swipe), we get the same picture again:

The lock screen does not wipe the encryption key after all.
After reverting to the password lock, I wanted to show a picture to one of my friends… but the SD card pictures were not recognised anymore.
Fourth mistake: The SD card encryption is disabled, the data not accessible. I restarted my phone, but the usual message that the SD card is encrypted didn’t pop up. And there is no option in the Android preferences to tell the system that the SD card is encrypted. The only option is to encrypt the SD card again. And that would double encrypt the already encrypted files. Fuuuu! So far I didn’t have enough time to check how I could restore the data, I might write a blog post about it, but for a start, check the Android source for the encryption. So far I copied down the encrypted files, but probably they’re unrecoverable. I guess the master key on the device was overwritten when I enabled encryption for the SD card again.
And I hate so say it, because there are too many Apple fan boys out there (I don’t need individuality, iPhone, iPhone, iPhone!), but: Yes, regarding device encryption, the newest iPhones are at least a little bit better. We are not talking about a device PIN of 4 digits, everybody knows that’s crap, but at least the disc is partially locked with this PIN when you lock your screen. It will protect your mail index, the keychain and files specially tagged by developers when your screen is locked. It’s a thought through concept of different encryption keys, although in the end that might not help that much (PIN bruteforcing, exploits, forensics…). Funny part is, that your mails won’t be stored encrypted on the iCloud (but that’s another story too). Well, let’s just say Apple is at least trying.
Unrelated fifth mistake: Factory Data Reset is totally broken for my phone. It was even better on my old Android 2.2, where it was at least deleting some stuff on the internal memory. That’s not the case for the Galaxy S3. I factory reset the device three times, it didn’t reset anything, just deleted the apps from the screens. All pictures, files, music, etc. is still on the internal and external memory. I wonder what it’s actually doing at all except from removing the icons from the different screens. Maybe this problem is because the phone was rooted once, but I properly unrooted it, so I doubt it.
Additionally, I found the login bypass for the Samsung Galaxy S3 here. Having some troubles, Galaxy S3?
Update: Also check this link to the details of the Android crypto implementation supplied by steentje in the comments.
Update2: Updated the iPhone part, as Jacob pointed out in the comments, Apple isn’t doing that well either.



