I’m a pretty happy owner of a Samsung Galaxy S3, Android Version 4.1.2. I don’t know if these things apply to the Galaxy S3 only, or if it’s the Android system that’s broken, but I’m pretty sure a lot of these things apply to all Android 4.1.2 phones.
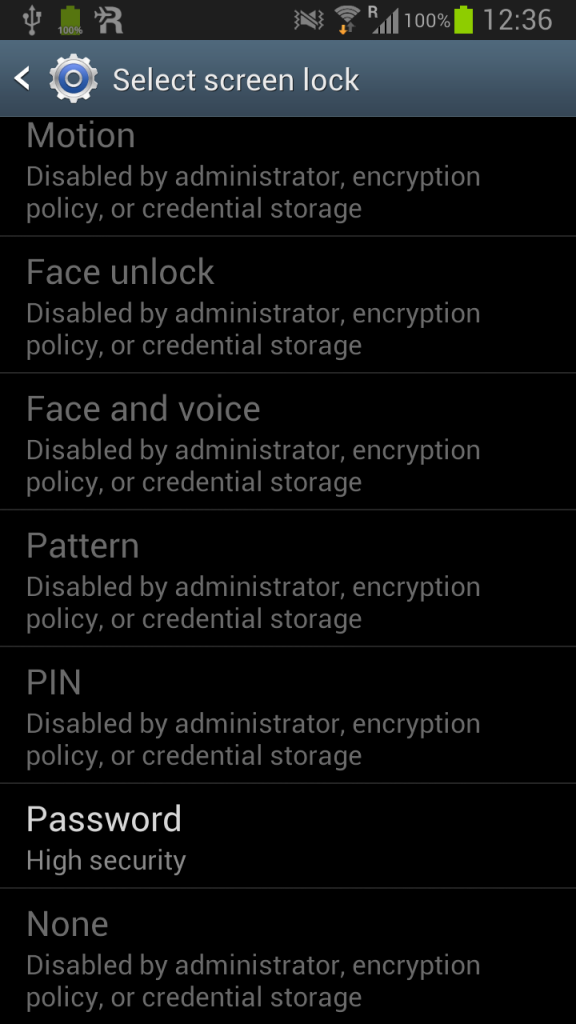
As you might have noticed I’m a little paranoid, so of course I want all security features enabled. Especially an encrypted internal memory and encrypted SD card is important. So while I wanted to set up the encryption for the internal memory, the device asked me to set up a lock screen password first, that contains at least one number.
First mistake. Why a number? There are enough reasons not to force such complexity rules. Maybe I would put a longer password in there with only lower and upper case. Now I have to press and hold one of the number buttons, which takes about 2 seconds. An alternative is to press 3 buttons to get a number. When you’re a fast typer you can type in 3 lowercase letters in that time, which is a lot stronger than having only a single number in it (if the attacker can still not rule out a number). Ok, whatever, let’s go on. But wait.
Second mistake. Why do I have to set up a lock screen password for device encryption? Answer: The disc encryption password is the lock screen password. Device encryption and lock screen are two different things. One scenario is a cold boot attack attacking the disc encryption password. The other one is when an attacker finds a device that is still running (let’s call it running device attack). If we want a shorter password for the lock screen for convenience reasons, then of course the security will decrease and running device attacks will get easier. But security does not decrease for cold boot attack scenarios if you’re able to use two different passwords. Of course you can argue that the running device attack is much more likely for mobile phones. But with some crypto you can easily make two different attack scenarios with different risks, depending on each password. So why do they have to be the same? The only conclusion I drawed at this point was that the disc encryption key will be properly wiped when the lock screen is enabled. So to unlock it you would need the disc encryption password (I was so wrong).
After setting the password I encrypted the SD card first, then the device. From that point on, I had to type in that long password every time I unlocked the screen. Annoying, but at least it’s secure as long as nobody is looking over my shoulder when I’m unlocking my phone (again, he would get the password for the cold boot AND the running device attack).
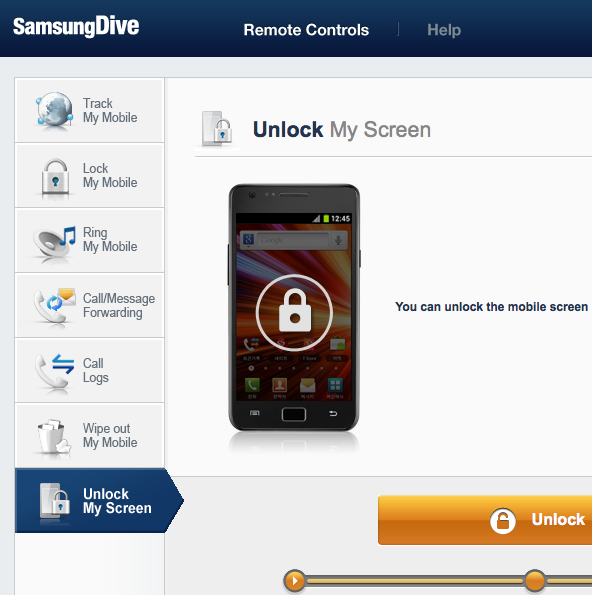
I took a month to think about the next security measure: Setting up SamsungDive. It’s the Samsung service where you can locate/wipe/ring your phone in case it got stolen or you lost it. I wasn’t sure if I wanted to do that. What if there is a security breach at samsungdive.com and somebody wipes my phone? And do I really want to give all that private information to Samsung? In the end I decided I wanted the feature anyway, so I set up a SamsungDive account. When I logged in, I realised there is another feature: Unlocking the screen remotely. Of course this would work for non-encrypted devices, but it won’t work for encrypted ones, because the encryption key was wiped when the screen was locked, right? Wrong.
Third mistake. The encryption key is not wiped when you lock your screen. It’s merely just to annoy the user that the lock screen password has to be the encryption password. After encrypting the device you can not change the lock screen type any more, everything is grayed out, except the password:
But let’s unlock the screen from the SamsungDive web site:
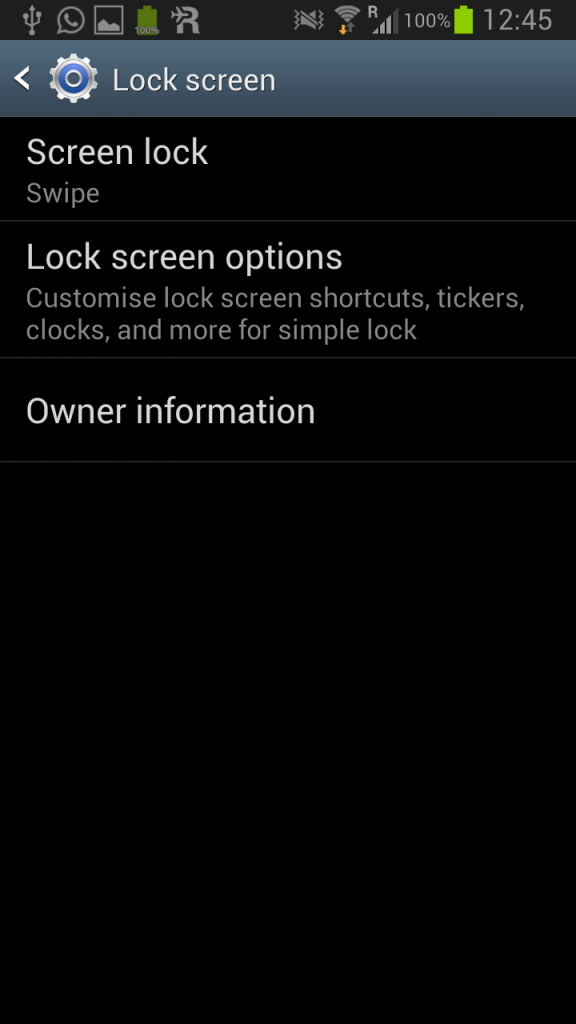
Now there is no screen lock anymore. Disabled. Gone. You don’t have to type in your password anymore. Look, swipe means no lock screen:
And when we want to change the type of lock screen mode again (clicking on Screen lock – Swipe), we get the same picture again:
The lock screen does not wipe the encryption key after all.
After reverting to the password lock, I wanted to show a picture to one of my friends… but the SD card pictures were not recognised anymore.
Fourth mistake: The SD card encryption is disabled, the data not accessible. I restarted my phone, but the usual message that the SD card is encrypted didn’t pop up. And there is no option in the Android preferences to tell the system that the SD card is encrypted. The only option is to encrypt the SD card again. And that would double encrypt the already encrypted files. Fuuuu! So far I didn’t have enough time to check how I could restore the data, I might write a blog post about it, but for a start, check the Android source for the encryption. So far I copied down the encrypted files, but probably they’re unrecoverable. I guess the master key on the device was overwritten when I enabled encryption for the SD card again.
And I hate so say it, because there are too many Apple fan boys out there (I don’t need individuality, iPhone, iPhone, iPhone!), but: Yes, regarding device encryption, the newest iPhones are at least a little bit better. We are not talking about a device PIN of 4 digits, everybody knows that’s crap, but at least the disc is partially locked with this PIN when you lock your screen. It will protect your mail index, the keychain and files specially tagged by developers when your screen is locked. It’s a thought through concept of different encryption keys, although in the end that might not help that much (PIN bruteforcing, exploits, forensics…). Funny part is, that your mails won’t be stored encrypted on the iCloud (but that’s another story too). Well, let’s just say Apple is at least trying.
Unrelated fifth mistake: Factory Data Reset is totally broken for my phone. It was even better on my old Android 2.2, where it was at least deleting some stuff on the internal memory. That’s not the case for the Galaxy S3. I factory reset the device three times, it didn’t reset anything, just deleted the apps from the screens. All pictures, files, music, etc. is still on the internal and external memory. I wonder what it’s actually doing at all except from removing the icons from the different screens. Maybe this problem is because the phone was rooted once, but I properly unrooted it, so I doubt it.
Additionally, I found the login bypass for the Samsung Galaxy S3 here. Having some troubles, Galaxy S3?
Update: Also check this link to the details of the Android crypto implementation supplied by steentje in the comments.
Update2: Updated the iPhone part, as Jacob pointed out in the comments, Apple isn’t doing that well either.

i also found that my motorola hands free bluetooth in the car, cannot use the voice recognition commands while the screen is locked (which is the case all the times).
in other words: i have to grab the phone (while driving) unlock it (with the looong passwd), then i can use voice recognition.
i have disabled the encryption feature, and beg the gods that my phone no to be stolen.
i did the same thing did you find a solution?
I have the exact same issue on my Samsung Galaxy S4 on Verizon that I just got! The problem for me is that it forces the unlock screen to use a password and not a pin code. This means that the input method is a keypad which is massively dangerous to use while doing other things (i.e. a 10 digit pin pad is much easier to use one handed). My old Galaxy Nexus let me use a 4 digit pin for the screen unlock even when the phone was encrypted. I am wondering if this is an issue in newer Android code? Or is this a stupidisim introduced by Samsung TouchWiz?
I just want stock Android on this phone running on the Verizon network! Google sells an unlocked stock S4 but it is only for GSM networks.
-Eric
“Unrelated fifth mistake: Factory Data Reset is totally broken for my phone. It was even better on my old Android 2.2, where it was at least deleting some stuff on the internal memory. That’s not the case for the Galaxy S3. I factory reset the device three times, it didn’t reset anything, just deleted the apps from the screens. All pictures, files, music, etc. is still on the internal and external memory. I wonder what it’s actually doing at all except from removing the icons from the different screens. Maybe this problem is because the phone was rooted once, but I properly unrooted it, so I doubt it.”
Hey, I have my phone root too, Im a security maniac and Im worry about whay you say because I have wiped several times and the files still there! I want something to change that, Cerberus app its good but without data connection is useless like Samsung dive … Im thinking of getting a hated iphone5 due to that security flaw… any chance to set the wipe thing to delete all internal? Or lock the phone like Blackberry, if you fail 10 times the cellphone DELETE EVERYTHING.
You mean the SD card encryption? Unfortunately not. Data lost for me. Although I didn’t try really hard to recover the data.
Need some help here. I have two sd cards. One for my daily use (32gb) and one for “personal” files (4gb). I encrypted my 4gb, removed it, inserted 32gb, encrypted it too as it was required, decrypted it coz i don’t want it to always be protected, and removed the screen lock password. Then, one day, when i wanted to use my 4gb which was encrypted, the pop-up i thought would appear, didn’t. And when i tried to open the files, they can’t be opened anymore. Even when i encrypt and decrypt it again, no use. I think you were talking about the same thing in your 4th mistake. Any thoughts?
Hi Jerrold,
The problem here is, that your SD card is not encrypted directly with your passphrase, but probably (I didn’t check the source code) with a key on the disc that is encrypted with your password. I guess the key for your 4GB card was overwritten when you set up the 32GB card, so no way of restoring. Therefore I doubt that your setup will work at all. And encrypting again was just encrypting already encrypted material again…
Too bad. Those files are precious to me. May of 2010 since i first started collecting those. I cant believe the one move i thought would secure them ruined them instead. I was hoping they could still be restored coz the thumbnails can still be viewed. My files are pictures and videos.
The thumbnails are still there? Maybe they are cached somewhere on the Android system. However, in the end it is hard to say what can be done without having the SD card here. I think you better use something like TrueCrypt next time.
Hi Jerrold,
You might be able to recover your files by manually mounting your SD card on a Linux distribution or a Mac which has the proper software. I’m assuming the encryption header is actually ON the SD card, which means that you should be able to decrypt your SD card without needing your phone, just using a Linux distro.
This is of course assuming you haven’t done anything to erase the encryption header yet, such as encrypting a second time, which would write a new encryption header.
Android uses cryptfs to encrypt the SD card, which also runs on normal Linux systems as far as I’m aware. I’ll see if I can find some more info on Google.
Now that I think of it, you might even be able to just manually mount it as root on your Galaxy S3 itself. That would be way easier than having to install a Linux distro on your computer. 🙂
Have you tried encrypting an empty SD card and then inserting your 4GB currently encrypted SD card? The encryption footer is stored in 16 KiB following the ext4 partition.
http://source.android.com/devices/tech/encryption/android_crypto_implementation.html
That describes Android tries to mount /data, and if it can’t, it assumes /data is encrypted. Maybe it will do the same for your SD card if you encrypt another empty one first. Maybe it will assume SD card is encrypted, ask for password to get the master key from the footer and then simply mount it.
Hi, I am using Samsung Galaxy Grand. My device was encrypted (Phone & External Memory). By mistakenly i have attempted wrong password and the device got factory reset. I lost my phone memory data however the i can see data in my memory card. but i cannot view those pictures, cant see videos and unable to open folders. can you tell me how to recover data from encrypted memory card after factory reset
hello floyd,i have the 4th mistake same problem …have u resolved the issue if yes plss share with us thanks,,,,
How long does it take to encrypt the SD card? I started the process on my device 2 days ago and it’s still going. However I have full functionality of the rest of my phone and it’s not using massive resources or anything. It’s not even draining the battery.
It just says it’s “Checking for errors” I can see which files have been encrypted as the icon app changes, but I can’t get to the “continue” button. The screen under ENCRYPT EXTERNAL SD CARD just says “wait until SD card encryption is completed. the “Turn off” and “Continue” button’s are greyed out.
I don’t know what to do. Help~?
I cried today for that encryption… i encrypted my SD card ..after using 2month i did factory reset without knowing the consequences, I Lost Every memories.. files are available but it Didnt showing anything… Those Or my Precious photos… Now trying to discrypt it..but I Coulnt. Somebody plz Tel that How discrypt my SD Card…
Guys.
Backups… keep backups of your data.
I usually charge my phone just by plugging it to my computer. I have setup a script that polls mounted disks every 1 minute. It runs rsync run each time I enable the phone to show the SD card contents and it copies all changed files to my raid1 array… which then by nightly backup is mirrored to off-site backup and to USB disk.
With linux.. it required me to write some bash and perl code. I assume there would be some ready setups if I had googled enuf.. but I had written similar code piece at work, so it was easy.
For windows.. well I fear you need to pay to get that done… but its small price to pay to keep your data safe. For mac.. I have no idea. I wont buy or even accept any iDevices.. but lets not go for the reasons of my mac-ban.
This way if I (or android) lose those encryption keys, I can still just format the SD card, re-setup encryption and just throw the files back on the card… ok on worst case I lose some files… but not all.
Sorry, but iOS encryption isnt that much better – see http://www.zdziarski.com/blog/?p=2149
Hi Jacob, agree, I also read Jonathan’s book and it seems Apple is having their own flaws. I’m going to update the post, although I think it’s still true that Apple is at least trying to protect some of the data.
Hi Floyd
Great article. Like you I am a bit of a security nut too. I have an Android 4.4.2 Galaxy S4 and I have tried encrypting it using this guide:
http://geoffboeing.com/2014/06/pattern-unlock-an-encrypted-android-phone/
This is meant to let you encrypt your phone but still be able to ues the pattern unlock screen. Didn’t work for me! It just kept rebooting the phone to the swipe screen and it was still unencrypted.
Do you know of any options or other ways that will let one fully encrypt an Android phone but let you use the pattern unlock screen? I don;t mind entering a longish password when I turn the phone on but when it comes to unlocking the phone at the unlock screen I want something more convenient as I will be unlocking the home screen dozens of times per day! (hence why a password is silly and a no no).
Any thoughts, ideas or recomendations on this? Great article!
Is there any new solution to bring back encrypted data after restoring on S3 (bought in Januray 2015) ?
Tab 3 encrypted but no key pad on screen to type in pass code. What do I do?
hello floyd, i came across this weblink in my search to undo decryption on my samsung i9505.
i wanted to remove the pin feature at boot and so chose the decrypt device from settings option.
after some time, i get a message saying – decryption failed and i have to reset to factory which will erase all data.
i have not done a backup and want to somehow gain access to my phone and extract all data before i click the reset phone option.
kindly help!